SPAM: Difference between revisions
No edit summary |
|||
| (16 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
== | ==Phishing and Email Scams== | ||
===Phishing=== | Phishing and other scam emails are an unfortunate and common reality in today’s digital world. The university regularly receives reports of attempts at email scams targeting WPUNJ accounts. | ||
These are often coordinated efforts by cybercriminals attempting to gain access to university email accounts using phishing emails that attempt to trick students and employees into providing their WPUNJ username and password information to the cybercriminals. | |||
===How can you help?=== | |||
The first step you can do is make sure your account is secure. See the information in the ‘What can I do to secure my account?’ section below on actions you can take to secure your account. | |||
The second step is to use always extra caution before clicking on any links or opening attachments in any email you receive from someone who you are either not familiar with or may not be expecting email from. When links in phishing emails are clicked, they usually load a webpage that looks real and asks for account username and password information. If that information is submitted, the cybercriminals then have access to that login information for the individual who filled out the account. Versions of these phishing emails usually: | |||
# Claim your account will be deactivated unless you click a link in the email to confirm your account. These may be sent from a WPUNJ email account after a scammer has successfully gained access to that account with a phishing email | |||
# Indicate that a document was shared with you and display the name of a colleague or someone else you may know. These are often Google Docs sharing emails sent from a compromised external Google account and primarily target faculty and staff | |||
If you receive an email like this, it's very likely to be a phishing email. If you have clicked a link in that email and then entered your username and/or password in a webpage that loaded, you should change your password immediately. | |||
You can report phishing or scam emails directly to Microsoft using the 'Report message' option in Outlook. They can also be reported to the Information Technology Helpdesk at www.wpunj.edu/helpdesk or (973) 720-4357. | |||
===What are these scammers after?=== | |||
In a word, money. Their main goal is to trick individuals for their own financial gain. It’s for this reason that we want to reinforce that it’s a WP community responsibility to be alert for phishing scams in order to protect our entire community from these scams. Once a scammer has access to login to an person’s account, they may attempt to use a variety of scams including: | |||
# Fake Job Scams: They use a compromised account to send emails to thousands of students and employees about ‘jobs’ that end up being a fake check scams intended to steal peoples’ money. This is the most common scam we’ve seen, with the goal being to trick students into believing they’ve been hired for a job and then scamming them of money by sending a fake check to deposit. The targets are told to keep part of the money and then send a larger portion on to someone else to cover the cost of supplies, training, or some other made up excuse. The fake check then will bounce multiple weeks later and the individual has then lost the money that was sent on to someone else. These are the worst kind of scams as they prey on our students. In prior years, we’ve had multiple cases of students who have been scammed out of thousands of dollars from this type of scam. | |||
# Bank Account Manipulation: Changing bank account information for direct deposits, student refunds, and even retirement accounts | |||
# Gift Card Scams: Scamming people by impersonating colleagues or friends, often requesting gift cards for some ‘urgent’ need or promise of extra credit | |||
===What is Phishing and how can I identify Phishing scams?=== | |||
Phishing is a technique that attempts to trick you into providing your username, password, or other private information. Phishing emails often include links that ask you to Click Here or View Document which then direct you to a fake website which will ask you to login or fill out a form with your information. That information is them collected by the scammers so they can login to your account. | |||
===What can I do to secure my account?=== | |||
The university has several proactive measures in place to attempt to safeguard against these types of attacks, but the most important role in securing your account is up to you. Here are a few key tips for maintaining a secure account. | |||
# Enroll in Duo multifactor authentication: The university uses Duo multifactor authentication (MFA) to provide an additional level of security for our accounts. If you have not yet enrolled in Duo, visit WPconnect and click on the Duo icon in the Apps menu to start the enrollment process. Duo enrollment is already required for all university employees, including student employees, and enrollment will be required for all students this semester. If you’ve enrolled in Duo and get a prompt to approve a login to your account that you didn’t initiate, deny the request and contact the IT Helpdesk immediately. | |||
# Know the scams: Review this ITWiki article on these scams to be familiar with the ways these scams work. | |||
# Change your password: If you haven’t changed your WPUNJ account password from the initial password you received, change it. This can be done in WPconnect by clicking on your name at the top right, then My Profile, and then Change My Password. | |||
#Report phishing and scam emails: suspicious messages can be reported directly to Microsoft using the 'Report Message' feature within the Outlook software, the web-based Outlook, and through the Outlook Mobile app. For additional information on how to submit a suspicious email to Microsoft for analysis, visit the 'Protect yourself from phishing' website located at https://support.microsoft.com/en-us/windows/protect-yourself-from-phishing-0c7ea947-ba98-3bd9-7184-430e1f860a44. | |||
===How can I get help if I need it?=== | |||
In attempt to control the spread of these scams, Information Technology will be aggressive with locking any account that shows sign of being compromised by scammers. Once an account has been identified as potentially compromised, login to that account will be blocked and our Helpdesk staff will follow up with the account holder to assist them with regaining access. | |||
If you or someone you know is unable to login to their WPUNJ account – or if you ever have questions about the legitimacy of an email you received – please contact our Information Technology Helpdesk at (973) 720-4357 or www.wpunj.edu/help, and one of our support staff members will be able to assist you. | |||
===What should I do if I've fallen for a phishing email or another scam?=== | |||
# Contact our IT Helpdesk at www.wpunj.edu/helpdesk or (973) 720-4357 for assistance and to report the scam | |||
# Immediately reset your password to something you have never used before. Our ITWiki article has some suggestions https://itwiki.wpunj.edu/index.php/Creating_a_Password_Pass_Phrase | |||
# Enroll in Duo multifactor authentication, through WPconnect, if you are not already enrolled | |||
# Check your email account's Inbox rules (under Settings) for rules set to forward your email to someone else or to delete all incoming email to your account | |||
# If you are a university employee, double check your records to sure your direct deposit information has not been altered | |||
===Types of Scam Emails=== | |||
====Phishing==== | |||
Phishing emails are fraudulent email messages that appear to be sent by legitimate sources (a friend or another student, the University IT department, a bank, etc.) These messages usually include a link to click on that directs you to malicious website made to look like a login page or a webform designed to get you to enter private information (for example, your username and password.) The attackers then use the information the information they've collected from you to commit some form of malicious activity with your account or, worse, identity theft. | Phishing emails are fraudulent email messages that appear to be sent by legitimate sources (a friend or another student, the University IT department, a bank, etc.) These messages usually include a link to click on that directs you to malicious website made to look like a login page or a webform designed to get you to enter private information (for example, your username and password.) The attackers then use the information the information they've collected from you to commit some form of malicious activity with your account or, worse, identity theft. | ||
Many phishing emails attempt to trick recipients by creating a sense or urgency with a threat that they will lose something unless they act quickly. Other phishing emails are designed to make it appear that the phishing email is part of a prior email communication, hoping the recipient will perceive the email as legitimate. | |||
Examples of wording using in Phishing emails include: | |||
*'Your account will be deactivated if you don't CLICK HERE.' | *'Your account will be deactivated if you don't CLICK HERE.' | ||
*'ACTION REQUIRED - MISSING FAFSA/Financial Aid Info. CLICK HERE for Document Review' | *'ACTION REQUIRED - MISSING FAFSA/Financial Aid Info. CLICK HERE for Document Review' | ||
| Line 10: | Line 64: | ||
*'You have received a secure document from XXX. Click Here to access.' | *'You have received a secure document from XXX. Click Here to access.' | ||
*'Unable to display full message. CLICK HERE to show full message.' | *'Unable to display full message. CLICK HERE to show full message.' | ||
[[File:PhishingEmailExample1.png|frame|center|Phishing Email Example]] | |||
For additional information on Phishing, visit one of these online resources: | For additional information on Phishing, visit one of these online resources: | ||
* https://www.phishing.org/what-is-phishing | * https://www.phishing.org/what-is-phishing | ||
*https://www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams | *https://www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams | ||
===Fake Part-Time Jobs & Fake Check Scams=== | ====Fake Part-Time Jobs & Fake Check Scams==== | ||
Many universities have been affected by students and employees receiving emails from other student emails or outside addresses that indicate that their company/friend/mother/uncle/etc. is hiring for a part-time job. | Many universities have been affected by students and employees receiving emails from other student emails or outside addresses that indicate that their company/friend/mother/uncle/etc. is hiring for a part-time job. | ||
*These 'jobs' range from pet or baby sitting to research or secret shopper jobs that students can do in their spare time to earn extra money. | *These 'jobs' range from pet or baby sitting to research or secret shopper jobs that students can do in their spare time to earn extra money. | ||
| Line 25: | Line 78: | ||
*A few weeks later, the initial check then does not clear and the individual who deposited the check is then out the money then sent on to someone else. | *A few weeks later, the initial check then does not clear and the individual who deposited the check is then out the money then sent on to someone else. | ||
[[File:FakeJob1.png|frame|center|Fake Part-Time Job Email]] | |||
[[File:Spam.png|1000 × 500px|frame|center|A pet sitting job scam on April 16th ]] | |||
Notice that this scam email in particular asks you to contact a secondary email rather than just replying to the one that sent the email. In addition, job advertisement scamming will usually include unrealistic salaries for doing an easy job to make it look more enticing. These are some easy signs to look out for. | |||
<br> | |||
[[File:Spam3.png|1000 x 500px|frame|center|Another job advertisement scam email on May 8th]] <br> | |||
Even though this job may not be for outside employment of the university, it still requests that you contact a secondary email for your response which should always raise suspicion. | |||
[[File:Spam2.png|1000 x 500px|frame|center|A phishing scam email on May 7th]] <br> | |||
A characteristic to watch out for when it comes to phishing scams is the amount of urgency that is repeated throughout the email’s entirety. The likelihood of the university to require all staff and students to migrate to a new Microsoft Outlook within 24 hours is extremely unlikely. | |||
For more information on fake check scams, visit the following links: | For more information on fake check scams, visit the following links: | ||
| Line 31: | Line 98: | ||
*https://www.bbb.org/pittsburgh/news-events/bbb-scam-alerts/2017/01/college-students-targeted-with-bogus-employment-offers/ | *https://www.bbb.org/pittsburgh/news-events/bbb-scam-alerts/2017/01/college-students-targeted-with-bogus-employment-offers/ | ||
===Impersonation Emails & Gift Card Scams=== | ====Impersonation Emails & Gift Card Scams==== | ||
Impersonation emails are emails that seem be sent by a trusted colleague or friend and start with a simple question like 'Are you available?' | Impersonation emails are emails that seem be sent by a trusted colleague or friend and start with a simple question like 'Are you available?' | ||
*These emails are sent so that they look like they are coming from the email of someone you know, but are actually sent from another email account used by a scammer. | *These emails are sent so that they look like they are coming from the email of someone you know, but are actually sent from another email account used by a scammer. | ||
| Line 38: | Line 104: | ||
*Usually, the request is to purchase gift cards for some urgent need they have and then scratch of the redemption codes and email or text pictures to them. | *Usually, the request is to purchase gift cards for some urgent need they have and then scratch of the redemption codes and email or text pictures to them. | ||
*Once the scammer has the redemption codes for the gift cards, the funds are immediate moved to another account and your money is now stolen. | *Once the scammer has the redemption codes for the gift cards, the funds are immediate moved to another account and your money is now stolen. | ||
[[File:ImpersonattionExample.png|frame|center|Impersonation Email Gift Card Scam Example]] | |||
For additional information on impersonation emails and gift card scams, please visit the following links: | For additional information on impersonation emails and gift card scams, please visit the following links: | ||
*https://www.chronicle.com/article/Phishing-Scheme-Targets/245535/ | *https://www.chronicle.com/article/Phishing-Scheme-Targets/245535/ | ||
*https://www.zdnet.com/article/beware-phony-gift-card-email-scams-heres-why-attackers-love-using-them/ | *https://www.zdnet.com/article/beware-phony-gift-card-email-scams-heres-why-attackers-love-using-them/ | ||
*https://www.cyber.nj.gov/garden_state_cyber_threat_highlight/gift-card-scams | |||
===Sextortion Emails=== | ====Sextortion Emails==== | ||
Sextortion scams are scams in which you receive an email from a 'hacker' that indicates the person has had access to your accounts and computers for several months and will release embarrassing photos/videos/search history to your friends, family, or coworkers unless you pay them some form of ransom (usually requested in Bitcoin.) The emails may even include part of a password you currently or previously used. | Sextortion scams are scams in which you receive an email from a 'hacker' that indicates the person has had access to your accounts and computers for several months and will release embarrassing photos/videos/search history to your friends, family, or coworkers unless you pay them some form of ransom (usually requested in Bitcoin.) The emails may even include part of a password you currently or previously used. | ||
| Line 49: | Line 117: | ||
'''While the emails may be scary to read, our recommendation is always to just ignore and delete the email.''' It's possible that you may receive several iterations of the email, but all can safely be ignored. | '''While the emails may be scary to read, our recommendation is always to just ignore and delete the email.''' It's possible that you may receive several iterations of the email, but all can safely be ignored. | ||
[[File:Sextortion Email Example.png|frame|center|Sextortion Email Example]] | |||
For more information on sextortion email scams, visit the following resources: | For more information on sextortion email scams, visit the following resources: | ||
* https://www.eff.org/deeplinks/2018/07/sextortion-scam-what-do-if-you-get-latest-phishing-spam-demanding-bitcoin | * https://www.eff.org/deeplinks/2018/07/sextortion-scam-what-do-if-you-get-latest-phishing-spam-demanding-bitcoin | ||
*https://www.cnbc.com/2019/06/17/email-sextortion-scams-on-the-rise-says-fbi.html | *https://www.cnbc.com/2019/06/17/email-sextortion-scams-on-the-rise-says-fbi.html | ||
https://en.wikipedia.org/wiki/Email_spam | https://en.wikipedia.org/wiki/Email_spam | ||
[[Category:Email]] | [[Category:Email]] | ||
Latest revision as of 09:10, 13 December 2023
Phishing and Email Scams
Phishing and other scam emails are an unfortunate and common reality in today’s digital world. The university regularly receives reports of attempts at email scams targeting WPUNJ accounts.
These are often coordinated efforts by cybercriminals attempting to gain access to university email accounts using phishing emails that attempt to trick students and employees into providing their WPUNJ username and password information to the cybercriminals.
How can you help?
The first step you can do is make sure your account is secure. See the information in the ‘What can I do to secure my account?’ section below on actions you can take to secure your account.
The second step is to use always extra caution before clicking on any links or opening attachments in any email you receive from someone who you are either not familiar with or may not be expecting email from. When links in phishing emails are clicked, they usually load a webpage that looks real and asks for account username and password information. If that information is submitted, the cybercriminals then have access to that login information for the individual who filled out the account. Versions of these phishing emails usually:
- Claim your account will be deactivated unless you click a link in the email to confirm your account. These may be sent from a WPUNJ email account after a scammer has successfully gained access to that account with a phishing email
- Indicate that a document was shared with you and display the name of a colleague or someone else you may know. These are often Google Docs sharing emails sent from a compromised external Google account and primarily target faculty and staff
If you receive an email like this, it's very likely to be a phishing email. If you have clicked a link in that email and then entered your username and/or password in a webpage that loaded, you should change your password immediately.
You can report phishing or scam emails directly to Microsoft using the 'Report message' option in Outlook. They can also be reported to the Information Technology Helpdesk at www.wpunj.edu/helpdesk or (973) 720-4357.
What are these scammers after?
In a word, money. Their main goal is to trick individuals for their own financial gain. It’s for this reason that we want to reinforce that it’s a WP community responsibility to be alert for phishing scams in order to protect our entire community from these scams. Once a scammer has access to login to an person’s account, they may attempt to use a variety of scams including:
- Fake Job Scams: They use a compromised account to send emails to thousands of students and employees about ‘jobs’ that end up being a fake check scams intended to steal peoples’ money. This is the most common scam we’ve seen, with the goal being to trick students into believing they’ve been hired for a job and then scamming them of money by sending a fake check to deposit. The targets are told to keep part of the money and then send a larger portion on to someone else to cover the cost of supplies, training, or some other made up excuse. The fake check then will bounce multiple weeks later and the individual has then lost the money that was sent on to someone else. These are the worst kind of scams as they prey on our students. In prior years, we’ve had multiple cases of students who have been scammed out of thousands of dollars from this type of scam.
- Bank Account Manipulation: Changing bank account information for direct deposits, student refunds, and even retirement accounts
- Gift Card Scams: Scamming people by impersonating colleagues or friends, often requesting gift cards for some ‘urgent’ need or promise of extra credit
What is Phishing and how can I identify Phishing scams?
Phishing is a technique that attempts to trick you into providing your username, password, or other private information. Phishing emails often include links that ask you to Click Here or View Document which then direct you to a fake website which will ask you to login or fill out a form with your information. That information is them collected by the scammers so they can login to your account.
What can I do to secure my account?
The university has several proactive measures in place to attempt to safeguard against these types of attacks, but the most important role in securing your account is up to you. Here are a few key tips for maintaining a secure account.
- Enroll in Duo multifactor authentication: The university uses Duo multifactor authentication (MFA) to provide an additional level of security for our accounts. If you have not yet enrolled in Duo, visit WPconnect and click on the Duo icon in the Apps menu to start the enrollment process. Duo enrollment is already required for all university employees, including student employees, and enrollment will be required for all students this semester. If you’ve enrolled in Duo and get a prompt to approve a login to your account that you didn’t initiate, deny the request and contact the IT Helpdesk immediately.
- Know the scams: Review this ITWiki article on these scams to be familiar with the ways these scams work.
- Change your password: If you haven’t changed your WPUNJ account password from the initial password you received, change it. This can be done in WPconnect by clicking on your name at the top right, then My Profile, and then Change My Password.
- Report phishing and scam emails: suspicious messages can be reported directly to Microsoft using the 'Report Message' feature within the Outlook software, the web-based Outlook, and through the Outlook Mobile app. For additional information on how to submit a suspicious email to Microsoft for analysis, visit the 'Protect yourself from phishing' website located at https://support.microsoft.com/en-us/windows/protect-yourself-from-phishing-0c7ea947-ba98-3bd9-7184-430e1f860a44.
How can I get help if I need it?
In attempt to control the spread of these scams, Information Technology will be aggressive with locking any account that shows sign of being compromised by scammers. Once an account has been identified as potentially compromised, login to that account will be blocked and our Helpdesk staff will follow up with the account holder to assist them with regaining access.
If you or someone you know is unable to login to their WPUNJ account – or if you ever have questions about the legitimacy of an email you received – please contact our Information Technology Helpdesk at (973) 720-4357 or www.wpunj.edu/help, and one of our support staff members will be able to assist you.
What should I do if I've fallen for a phishing email or another scam?
- Contact our IT Helpdesk at www.wpunj.edu/helpdesk or (973) 720-4357 for assistance and to report the scam
- Immediately reset your password to something you have never used before. Our ITWiki article has some suggestions https://itwiki.wpunj.edu/index.php/Creating_a_Password_Pass_Phrase
- Enroll in Duo multifactor authentication, through WPconnect, if you are not already enrolled
- Check your email account's Inbox rules (under Settings) for rules set to forward your email to someone else or to delete all incoming email to your account
- If you are a university employee, double check your records to sure your direct deposit information has not been altered
Types of Scam Emails
Phishing
Phishing emails are fraudulent email messages that appear to be sent by legitimate sources (a friend or another student, the University IT department, a bank, etc.) These messages usually include a link to click on that directs you to malicious website made to look like a login page or a webform designed to get you to enter private information (for example, your username and password.) The attackers then use the information the information they've collected from you to commit some form of malicious activity with your account or, worse, identity theft.
Many phishing emails attempt to trick recipients by creating a sense or urgency with a threat that they will lose something unless they act quickly. Other phishing emails are designed to make it appear that the phishing email is part of a prior email communication, hoping the recipient will perceive the email as legitimate.
Examples of wording using in Phishing emails include:
- 'Your account will be deactivated if you don't CLICK HERE.'
- 'ACTION REQUIRED - MISSING FAFSA/Financial Aid Info. CLICK HERE for Document Review'
- 'A file has been shared with you. ONEDRIVE Document.'
- 'You have received a secure document from XXX. Click Here to access.'
- 'Unable to display full message. CLICK HERE to show full message.'
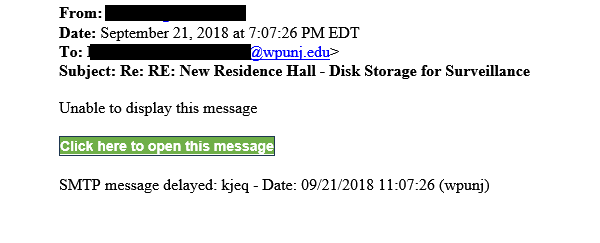
For additional information on Phishing, visit one of these online resources:
- https://www.phishing.org/what-is-phishing
- https://www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams
Fake Part-Time Jobs & Fake Check Scams
Many universities have been affected by students and employees receiving emails from other student emails or outside addresses that indicate that their company/friend/mother/uncle/etc. is hiring for a part-time job.
- These 'jobs' range from pet or baby sitting to research or secret shopper jobs that students can do in their spare time to earn extra money.
- These are fake job scams that attempt to have individuals deposit a fake check.
- Students who reply and indicate interest receive responses asking to provide detailed contact information (address, date of birth, etc.)
- The scammers then indicate that you are 'hired' and send a fake check or money order to "cover start up wages/supplies."
- The check is often for $1,500-2,000, and the student is asked to keep some of the money as their payment and sent the larger remaining about of money from the check to someone else via gift card, wire transfer, or other means.
- A few weeks later, the initial check then does not clear and the individual who deposited the check is then out the money then sent on to someone else.
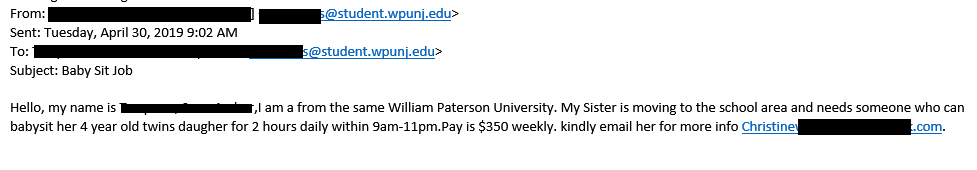
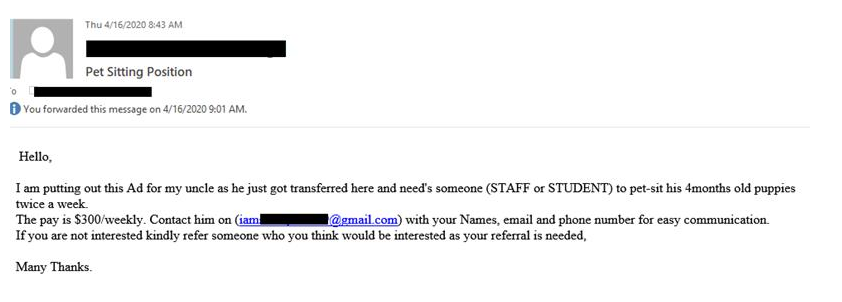
Notice that this scam email in particular asks you to contact a secondary email rather than just replying to the one that sent the email. In addition, job advertisement scamming will usually include unrealistic salaries for doing an easy job to make it look more enticing. These are some easy signs to look out for.
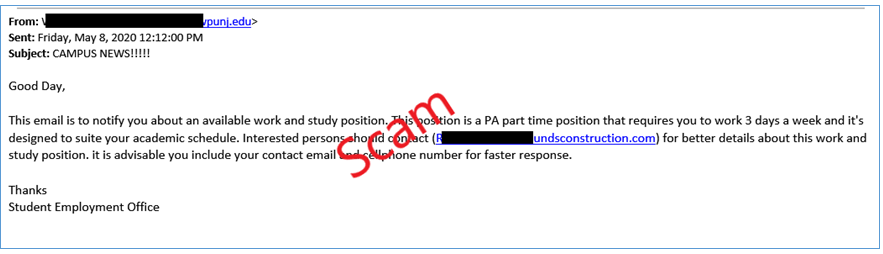
Even though this job may not be for outside employment of the university, it still requests that you contact a secondary email for your response which should always raise suspicion.
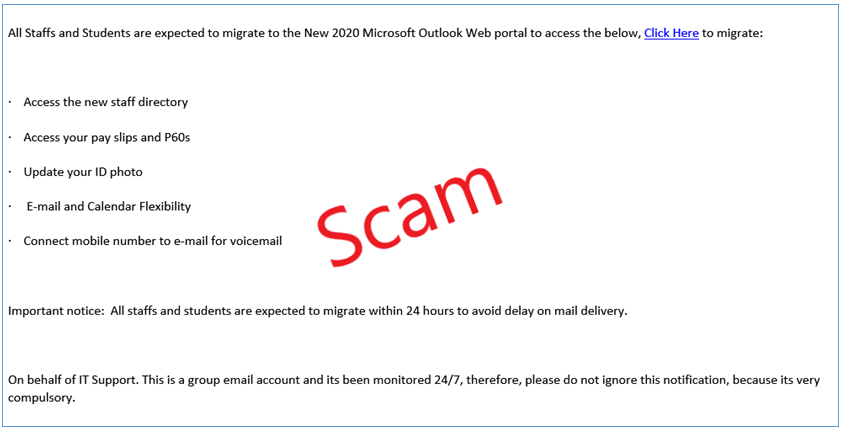
A characteristic to watch out for when it comes to phishing scams is the amount of urgency that is repeated throughout the email’s entirety. The likelihood of the university to require all staff and students to migrate to a new Microsoft Outlook within 24 hours is extremely unlikely.
For more information on fake check scams, visit the following links:
- https://www.fraud.org/fake_check_scams
- https://www.ic3.gov/media/2017/170118.aspx
- https://www.bbb.org/pittsburgh/news-events/bbb-scam-alerts/2017/01/college-students-targeted-with-bogus-employment-offers/
Impersonation Emails & Gift Card Scams
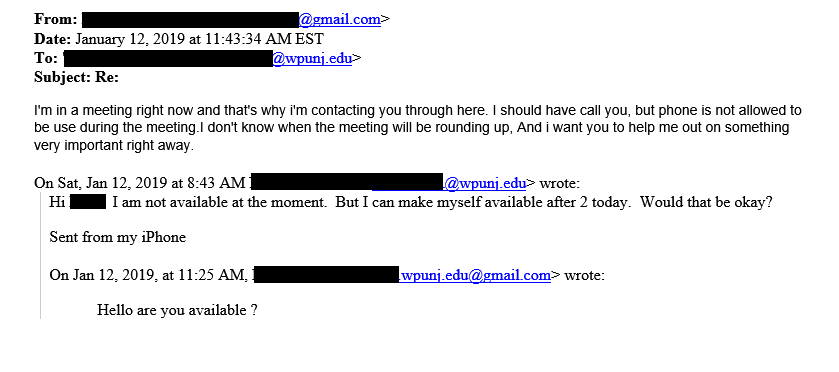
Impersonation emails are emails that seem be sent by a trusted colleague or friend and start with a simple question like 'Are you available?'
- These emails are sent so that they look like they are coming from the email of someone you know, but are actually sent from another email account used by a scammer.
- If you reply to the email, you'll be asked if you can do a favor for that person.
- Usually, the request is to purchase gift cards for some urgent need they have and then scratch of the redemption codes and email or text pictures to them.
- Once the scammer has the redemption codes for the gift cards, the funds are immediate moved to another account and your money is now stolen.
For additional information on impersonation emails and gift card scams, please visit the following links:
- https://www.chronicle.com/article/Phishing-Scheme-Targets/245535/
- https://www.zdnet.com/article/beware-phony-gift-card-email-scams-heres-why-attackers-love-using-them/
- https://www.cyber.nj.gov/garden_state_cyber_threat_highlight/gift-card-scams
Sextortion Emails
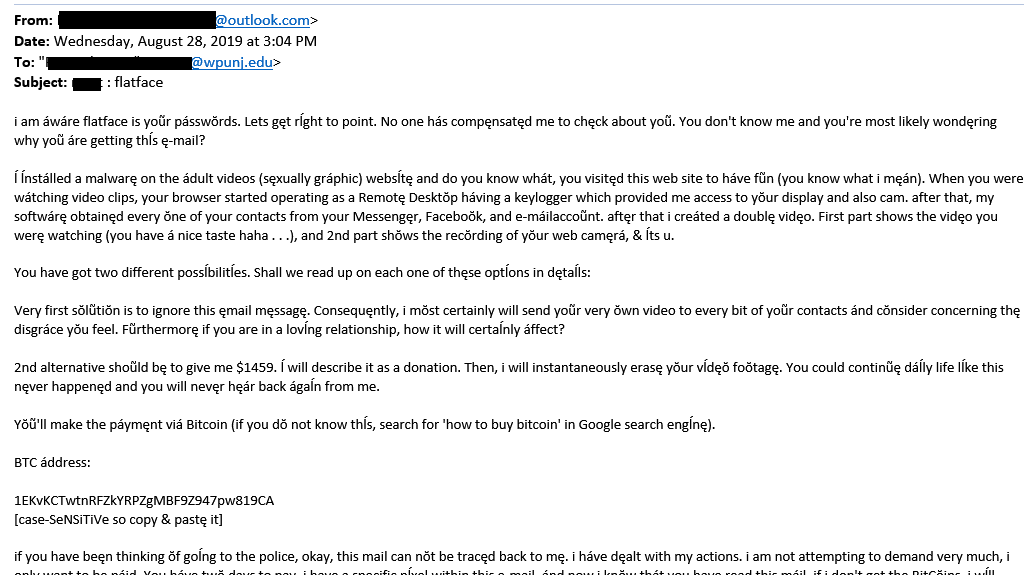
Sextortion scams are scams in which you receive an email from a 'hacker' that indicates the person has had access to your accounts and computers for several months and will release embarrassing photos/videos/search history to your friends, family, or coworkers unless you pay them some form of ransom (usually requested in Bitcoin.) The emails may even include part of a password you currently or previously used.
These emails are rarely ever legitimate. In most cases, the emails are sent to individuals by the thousands using lists of emails - and possibly passwords - compiled from website hacks over the years. While the emails may be scary to read, our recommendation is always to just ignore and delete the email. It's possible that you may receive several iterations of the email, but all can safely be ignored.
For more information on sextortion email scams, visit the following resources: